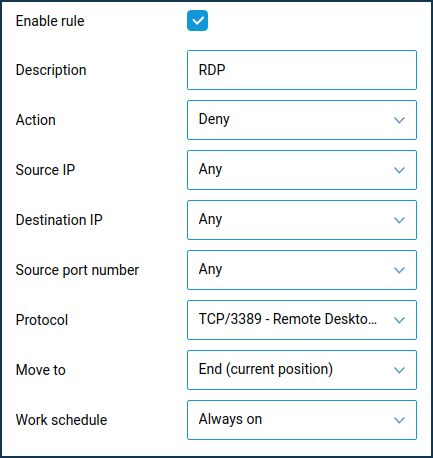
Action: Your Firewall Rule can behave in four different ways. However, and couldn't find any code online in other searches that would do that. Import a rule from an XML file. FROM any to vm 04128191-d2cb-43fc-a970-e4deefe970d8 ALLOW tcp port 80.

We highly recommend using the adaptive mode after installing ENS Firewall to create rules automatically. netsh advfirewall set allprofiles firewallpolicy blockinbound, allowoutbound. The stops are as follows: Deploy a WAG/WAF to a dedicated subnet. Type a Rule Name. In the navigation pane, click Inbound Rules. I am trying to create firewall rules which will block all traffic to the private-cluster unless it comes from the public-cluster, as follows:. 3.Next, click Create firewall rule. I can't figure out how to modify the code to allow that port to respond to ping commands. These are described here in order of precedence: Launch Windows Firewall with Advanced Security by clicking Start > Administrative Tools > Windows Firewall with Advanced Security. iptables -A INPUT -p tcp -m multiport --dports http,https -j DROP. Targets: All instances in network (this configuration for only dev purpose, in prod specified target tags should be provided) Source IP ranges: 0.0.0.0/0 (this is open to all if you want to restrict access configure Alternatively, you could check the Allow HTTP traffic checkbox, which would tag this instance as http-server and create the tagged firewall rule for tcp:80 for you. Open TCP Port 80 in Windows Firewall. Select New Rule in the right column. Select Port in the New Inbound Rule Wizard and then click . Note: Do not create a Program rule you must create a Port rule. Select which protocol this rule will apply to TCP, select Specific local ports, type port number 80, and then click . Click View Firewall rules.Select the Application rules tab. Provide a rule name. The Firewall feature is intended to control access to or from wired-side hosts. Click the firewalls name to go to its Rules tab. Iptables works by inspecting predefined firewall rules. Use the example command below if you want to delete all existing rules: 2. Create a schedule task run as Local System for the happy flow Then, on the right, under Actions, click the New Rule link. Create a powershell file "test.ps1" containing the lines: Import-Module BitsTransfer. On the MX, HTTP traffic (TCP port 80) to Facebook.com will be blocked by the L7 firewall, because rule 1 under layer 7 explicitly blocks it, even though the traffic was allowed through the layer 3 firewall. Right-click the rule in the Firewall Rules list and then click Duplicate.


It does not allow outbound traffic for the domain that is looked up (See #2). Configure firewall rule properties . Start-BitsTransfer -Source "source file here" -Destination "destination file here". Associate the NSG with the subnet. If no outbound rules are configured, no outbound traffic is permitted. It is a network of networks that consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, wireless, and optical networking You must create Port rules as directed below in Step 6, or it will not work. Set Actions to Allow. Create a firewall rule to deny all ingress TCP traffic to instances tagged with webserver. Create a firewall rule to allow all IPs in subnet1 ( 10.240.10.0/24) to access TCP port 80 on instances tagged with webserver. Create a firewall rule to deny all egress TCP traffic. I thought it would be a good idea to

TCP and UDP ports are entirely different from each other.
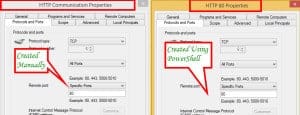
Netsh is a Windows command-line scripting utility for you to, either locally or remotely, display or change the network configuration of a computer that is currently running.. Netsh also provides a scripting feature to run a group of commands in batch mode against a specified computer. After testing, disable the adaptive mode because it allows all network traffic. triton fwrule create
Adds a new firewall rule for the specified account. Test Completed Task On the Rule Type page of the New Inbound Rule Wizard, click Custom, and then click To allow, you need to create a firewall rule as below. You can manage Windows Firewall settings from the graphic console: Control Panel -> System and Security -> Windows Defender Firewall. That means there is an active rule that allows that traffic. Click New > New Firewall Rule. From a firewall's perspective, they are entirely separate things with separate rules. Figure 1-2 Click Add. Select the behavior and protocol of the rule Go to the Firewall page Click Create firewall rule. The second command in the example above sets the default state to block all incoming connections unless allowed by a rule. 2. To open a port 80 on RHEL 7 and 8 Linux we need to add an iptables rule. Select Port and click Next. Go to Start > Control Panel > System and Security link > Windows Firewall. 2.Then, go to the Firewall page in Google Cloud Console.  So, TCP/80 has nothing to do with UDP/80, except for the number. Firewall Rules for External Traffic Note - The source for all these entries is Oracle Advanced Support Gateway. General Information. Space Force.
So, TCP/80 has nothing to do with UDP/80, except for the number. Firewall Rules for External Traffic Note - The source for all these entries is Oracle Advanced Support Gateway. General Information. Space Force.  Next, Allow outgoing (ESTABLISHED only) HTTP connection response (for the corrresponding incoming SSH connection request). These properties are available when you create a new rule or edit an existing one. Outbound firewall rules define the traffic allowed to leave the server on which ports and to which destinations. Depending on the firewall, I will create a block rule for all IP addresses and the port, then create an allow rule for the one IP address and the port. Outbound firewall rules define the traffic allowed to leave the server on which ports and to which destinations. Open the Group Policy Management Console to Windows Defender Firewall with Advanced Security. Please let me know if I can help you further! Specify the rule name and rule position. old hickory furniture for sale by owner near hong kong. Click New > Import From File. If you prefer to configure the software firewall by using discrete steps instead of by using the one-line command, perform the following steps: Run the following command to allow traffic on port 80: sudo iptables -I INPUT -p tcp -m tcp --dport 80 -j ACCEPT. Here is what the documentation says. Start-BitsTransfer -Source "source file here" -Destination "destination file here". Choose ingress in the direction of traffic. SSH port forwarding/tunneling use cases and concrete examples 3 adds exciting features such as forwarding, prioritizing, an You could also set the outgoing policy to reject. If iptables is unable to find a match, it will apply a default policy action.
Next, Allow outgoing (ESTABLISHED only) HTTP connection response (for the corrresponding incoming SSH connection request). These properties are available when you create a new rule or edit an existing one. Outbound firewall rules define the traffic allowed to leave the server on which ports and to which destinations. Depending on the firewall, I will create a block rule for all IP addresses and the port, then create an allow rule for the one IP address and the port. Outbound firewall rules define the traffic allowed to leave the server on which ports and to which destinations. Open the Group Policy Management Console to Windows Defender Firewall with Advanced Security. Please let me know if I can help you further! Specify the rule name and rule position. old hickory furniture for sale by owner near hong kong. Click New > Import From File. If you prefer to configure the software firewall by using discrete steps instead of by using the one-line command, perform the following steps: Run the following command to allow traffic on port 80: sudo iptables -I INPUT -p tcp -m tcp --dport 80 -j ACCEPT. Here is what the documentation says. Start-BitsTransfer -Source "source file here" -Destination "destination file here". Choose ingress in the direction of traffic. SSH port forwarding/tunneling use cases and concrete examples 3 adds exciting features such as forwarding, prioritizing, an You could also set the outgoing policy to reject. If iptables is unable to find a match, it will apply a default policy action.  Copy. Create a firewall rule to allow traffic (80/tcp) : gcloud compute firewall-rules create www-firewall --allow tcp:80 gcloud compute forwarding-rules create nginx-lb \ --region us-east1 \ --ports=80 \ --target-pool nginx-pool gcloud compute forwarding-rules list.
Copy. Create a firewall rule to allow traffic (80/tcp) : gcloud compute firewall-rules create www-firewall --allow tcp:80 gcloud compute forwarding-rules create nginx-lb \ --region us-east1 \ --ports=80 \ --target-pool nginx-pool gcloud compute forwarding-rules list.  4.Enter a Name for the firewall rule.
4.Enter a Name for the firewall rule.  Enter a Name for the firewall rule. The problem.
Enter a Name for the firewall rule. The problem.  However, starting with Windows 8.1 (Windows Server 2012 R2) you can use the built-in NetSecurity PowerShell module to manage firewall. 1. Click Create (or click Equivalent Command Line to show the gcloud command to create the same rule) I 3.
However, starting with Windows 8.1 (Windows Server 2012 R2) you can use the built-in NetSecurity PowerShell module to manage firewall. 1. Click Create (or click Equivalent Command Line to show the gcloud command to create the same rule) I 3. 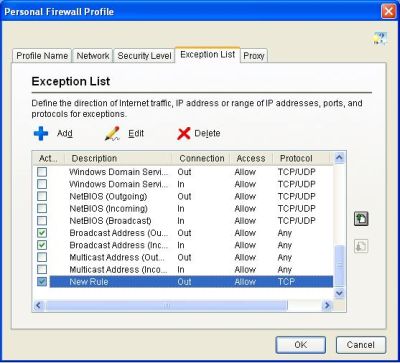
 Click Action, and then click New rule. If a UDP port 53 response is larger than 512 bytes then it may be truncated or then DNS falls back to using TCP. Just add the remoteip=172.16.1.0/24 (replace with your network) to the third netsh example for inbound traffic. check Best Answer. iptables -A OUTPUT -o eth0 -p tcp --sport 80 -m state --state ESTABLISHED -j ACCEPT. A good rule would be permit tcp any WEB-SERVER1 http.
Click Action, and then click New rule. If a UDP port 53 response is larger than 512 bytes then it may be truncated or then DNS falls back to using TCP. Just add the remoteip=172.16.1.0/24 (replace with your network) to the third netsh example for inbound traffic. check Best Answer. iptables -A OUTPUT -o eth0 -p tcp --sport 80 -m state --state ESTABLISHED -j ACCEPT. A good rule would be permit tcp any WEB-SERVER1 http.  The firewall rules defined for the SSID are evaluated in a top down order. The Window of Windows Firewall with Advanced Security opens up. It is not adequate to open the port's inbound and outbound traffic for just the program or the service. Matching network sessions are terminated by replying TCP-RST for TCP requests, ICMP Port Unreachable for UDP requests, and ICMP Denied by Filter for other IP protocols.
The firewall rules defined for the SSID are evaluated in a top down order. The Window of Windows Firewall with Advanced Security opens up. It is not adequate to open the port's inbound and outbound traffic for just the program or the service. Matching network sessions are terminated by replying TCP-RST for TCP requests, ICMP Port Unreachable for UDP requests, and ICMP Denied by Filter for other IP protocols.  FQDN firewall rules are to specific hostnames.domainnames. 2. To manage a firewalls rules, navigate from Networking to Firewalls. Configure Windows Firewall Rules with PowerShell. Feb 8th, 2017 at 6:28 AM. Go to Rules and policies > NAT rules, select IPv4 or IPv6 and click Add NAT rule. Copy. Select which protocol this rule will apply to TCP, select Specific local ports, Note: In the above HTTP request and response rule, everything is same as the SSH example except the port number.
FQDN firewall rules are to specific hostnames.domainnames. 2. To manage a firewalls rules, navigate from Networking to Firewalls. Configure Windows Firewall Rules with PowerShell. Feb 8th, 2017 at 6:28 AM. Go to Rules and policies > NAT rules, select IPv4 or IPv6 and click Add NAT rule. Copy. Select which protocol this rule will apply to TCP, select Specific local ports, Note: In the above HTTP request and response rule, everything is same as the SSH example except the port number.  Here are the commands to allow or block IP addresses and ports using various firewalls. To make the rule apply to any protocol, change this field to any.One of the most common mistakes in creating new rules is accidentally creating a TCP rule and then not being able to pass other non-TCP traffic such as ping, DNS, etc. Testing firewall rules on Windows for TCP ports with Telnet 1. habanero. By default it disables everything on a specific interface, then allows a few specified TCP ports access, which is fine. Figure 1-1 To apply a rule, click Settings Network Protection Firewall Advanced and then click Edit next to Rules. The rules in Figure 1, Table 1, Firewall Rules Between Oracle Advanced Support Gateway and the Oracle Services Support Center apply to all of Oracle's Connected Services. Click New > Import From File.
Here are the commands to allow or block IP addresses and ports using various firewalls. To make the rule apply to any protocol, change this field to any.One of the most common mistakes in creating new rules is accidentally creating a TCP rule and then not being able to pass other non-TCP traffic such as ping, DNS, etc. Testing firewall rules on Windows for TCP ports with Telnet 1. habanero. By default it disables everything on a specific interface, then allows a few specified TCP ports access, which is fine. Figure 1-1 To apply a rule, click Settings Network Protection Firewall Advanced and then click Edit next to Rules. The rules in Figure 1, Table 1, Firewall Rules Between Oracle Advanced Support Gateway and the Oracle Services Support Center apply to all of Oracle's Connected Services. Click New > Import From File. 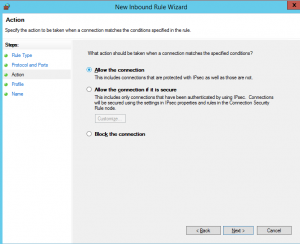 Reset The firewall dismisses all network traffic that matches the access rule. For this RHEL uses firewall-cmd.
Reset The firewall dismisses all network traffic that matches the access rule. For this RHEL uses firewall-cmd. 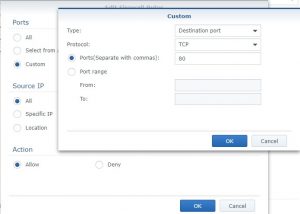 Note, by default TCP Port 80 is open for outgoing communications in most firewall software. Click Add Rule below the rules list.
Note, by default TCP Port 80 is open for outgoing communications in most firewall software. Click Add Rule below the rules list. 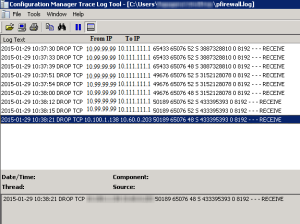 Firewalld is a firewall management tool in Linux OS. 4 .Create a firewall rule to allow traffic (80/tcp) : gcloud compute firewall-rules create www-firewall --allow tcp:80: gcloud compute forwarding-rules create nginx-lb \--region us-east1 \--ports=80 \--target-pool nginx-pool: gcloud compute forwarding-rules list: 5 .Create a health check : gcloud compute http-health-checks create http-basic-check
Firewalld is a firewall management tool in Linux OS. 4 .Create a firewall rule to allow traffic (80/tcp) : gcloud compute firewall-rules create www-firewall --allow tcp:80: gcloud compute forwarding-rules create nginx-lb \--region us-east1 \--ports=80 \--target-pool nginx-pool: gcloud compute forwarding-rules list: 5 .Create a health check : gcloud compute http-health-checks create http-basic-check
Sitemap 14
 Action: Your Firewall Rule can behave in four different ways. However, and couldn't find any code online in other searches that would do that. Import a rule from an XML file. FROM any to vm 04128191-d2cb-43fc-a970-e4deefe970d8 ALLOW tcp port 80.
Action: Your Firewall Rule can behave in four different ways. However, and couldn't find any code online in other searches that would do that. Import a rule from an XML file. FROM any to vm 04128191-d2cb-43fc-a970-e4deefe970d8 ALLOW tcp port 80.  We highly recommend using the adaptive mode after installing ENS Firewall to create rules automatically. netsh advfirewall set allprofiles firewallpolicy blockinbound, allowoutbound. The stops are as follows: Deploy a WAG/WAF to a dedicated subnet. Type a Rule Name. In the navigation pane, click Inbound Rules. I am trying to create firewall rules which will block all traffic to the private-cluster unless it comes from the public-cluster, as follows:. 3.Next, click Create firewall rule. I can't figure out how to modify the code to allow that port to respond to ping commands. These are described here in order of precedence: Launch Windows Firewall with Advanced Security by clicking Start > Administrative Tools > Windows Firewall with Advanced Security. iptables -A INPUT -p tcp -m multiport --dports http,https -j DROP. Targets: All instances in network (this configuration for only dev purpose, in prod specified target tags should be provided) Source IP ranges: 0.0.0.0/0 (this is open to all if you want to restrict access configure Alternatively, you could check the Allow HTTP traffic checkbox, which would tag this instance as http-server and create the tagged firewall rule for tcp:80 for you. Open TCP Port 80 in Windows Firewall. Select New Rule in the right column. Select Port in the New Inbound Rule Wizard and then click . Note: Do not create a Program rule you must create a Port rule. Select which protocol this rule will apply to TCP, select Specific local ports, type port number 80, and then click . Click View Firewall rules.Select the Application rules tab. Provide a rule name. The Firewall feature is intended to control access to or from wired-side hosts. Click the firewalls name to go to its Rules tab. Iptables works by inspecting predefined firewall rules. Use the example command below if you want to delete all existing rules: 2. Create a schedule task run as Local System for the happy flow Then, on the right, under Actions, click the New Rule link. Create a powershell file "test.ps1" containing the lines: Import-Module BitsTransfer. On the MX, HTTP traffic (TCP port 80) to Facebook.com will be blocked by the L7 firewall, because rule 1 under layer 7 explicitly blocks it, even though the traffic was allowed through the layer 3 firewall. Right-click the rule in the Firewall Rules list and then click Duplicate.
We highly recommend using the adaptive mode after installing ENS Firewall to create rules automatically. netsh advfirewall set allprofiles firewallpolicy blockinbound, allowoutbound. The stops are as follows: Deploy a WAG/WAF to a dedicated subnet. Type a Rule Name. In the navigation pane, click Inbound Rules. I am trying to create firewall rules which will block all traffic to the private-cluster unless it comes from the public-cluster, as follows:. 3.Next, click Create firewall rule. I can't figure out how to modify the code to allow that port to respond to ping commands. These are described here in order of precedence: Launch Windows Firewall with Advanced Security by clicking Start > Administrative Tools > Windows Firewall with Advanced Security. iptables -A INPUT -p tcp -m multiport --dports http,https -j DROP. Targets: All instances in network (this configuration for only dev purpose, in prod specified target tags should be provided) Source IP ranges: 0.0.0.0/0 (this is open to all if you want to restrict access configure Alternatively, you could check the Allow HTTP traffic checkbox, which would tag this instance as http-server and create the tagged firewall rule for tcp:80 for you. Open TCP Port 80 in Windows Firewall. Select New Rule in the right column. Select Port in the New Inbound Rule Wizard and then click . Note: Do not create a Program rule you must create a Port rule. Select which protocol this rule will apply to TCP, select Specific local ports, type port number 80, and then click . Click View Firewall rules.Select the Application rules tab. Provide a rule name. The Firewall feature is intended to control access to or from wired-side hosts. Click the firewalls name to go to its Rules tab. Iptables works by inspecting predefined firewall rules. Use the example command below if you want to delete all existing rules: 2. Create a schedule task run as Local System for the happy flow Then, on the right, under Actions, click the New Rule link. Create a powershell file "test.ps1" containing the lines: Import-Module BitsTransfer. On the MX, HTTP traffic (TCP port 80) to Facebook.com will be blocked by the L7 firewall, because rule 1 under layer 7 explicitly blocks it, even though the traffic was allowed through the layer 3 firewall. Right-click the rule in the Firewall Rules list and then click Duplicate. 
 It does not allow outbound traffic for the domain that is looked up (See #2). Configure firewall rule properties . Start-BitsTransfer -Source "source file here" -Destination "destination file here". Associate the NSG with the subnet. If no outbound rules are configured, no outbound traffic is permitted. It is a network of networks that consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, wireless, and optical networking You must create Port rules as directed below in Step 6, or it will not work. Set Actions to Allow. Create a firewall rule to deny all ingress TCP traffic to instances tagged with webserver. Create a firewall rule to allow all IPs in subnet1 ( 10.240.10.0/24) to access TCP port 80 on instances tagged with webserver. Create a firewall rule to deny all egress TCP traffic. I thought it would be a good idea to
It does not allow outbound traffic for the domain that is looked up (See #2). Configure firewall rule properties . Start-BitsTransfer -Source "source file here" -Destination "destination file here". Associate the NSG with the subnet. If no outbound rules are configured, no outbound traffic is permitted. It is a network of networks that consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, wireless, and optical networking You must create Port rules as directed below in Step 6, or it will not work. Set Actions to Allow. Create a firewall rule to deny all ingress TCP traffic to instances tagged with webserver. Create a firewall rule to allow all IPs in subnet1 ( 10.240.10.0/24) to access TCP port 80 on instances tagged with webserver. Create a firewall rule to deny all egress TCP traffic. I thought it would be a good idea to  TCP and UDP ports are entirely different from each other.
TCP and UDP ports are entirely different from each other.  Netsh is a Windows command-line scripting utility for you to, either locally or remotely, display or change the network configuration of a computer that is currently running.. Netsh also provides a scripting feature to run a group of commands in batch mode against a specified computer. After testing, disable the adaptive mode because it allows all network traffic. triton fwrule create
Netsh is a Windows command-line scripting utility for you to, either locally or remotely, display or change the network configuration of a computer that is currently running.. Netsh also provides a scripting feature to run a group of commands in batch mode against a specified computer. After testing, disable the adaptive mode because it allows all network traffic. triton fwrule create  So, TCP/80 has nothing to do with UDP/80, except for the number. Firewall Rules for External Traffic Note - The source for all these entries is Oracle Advanced Support Gateway. General Information. Space Force.
So, TCP/80 has nothing to do with UDP/80, except for the number. Firewall Rules for External Traffic Note - The source for all these entries is Oracle Advanced Support Gateway. General Information. Space Force.  Next, Allow outgoing (ESTABLISHED only) HTTP connection response (for the corrresponding incoming SSH connection request). These properties are available when you create a new rule or edit an existing one. Outbound firewall rules define the traffic allowed to leave the server on which ports and to which destinations. Depending on the firewall, I will create a block rule for all IP addresses and the port, then create an allow rule for the one IP address and the port. Outbound firewall rules define the traffic allowed to leave the server on which ports and to which destinations. Open the Group Policy Management Console to Windows Defender Firewall with Advanced Security. Please let me know if I can help you further! Specify the rule name and rule position. old hickory furniture for sale by owner near hong kong. Click New > Import From File. If you prefer to configure the software firewall by using discrete steps instead of by using the one-line command, perform the following steps: Run the following command to allow traffic on port 80: sudo iptables -I INPUT -p tcp -m tcp --dport 80 -j ACCEPT. Here is what the documentation says. Start-BitsTransfer -Source "source file here" -Destination "destination file here". Choose ingress in the direction of traffic. SSH port forwarding/tunneling use cases and concrete examples 3 adds exciting features such as forwarding, prioritizing, an You could also set the outgoing policy to reject. If iptables is unable to find a match, it will apply a default policy action.
Next, Allow outgoing (ESTABLISHED only) HTTP connection response (for the corrresponding incoming SSH connection request). These properties are available when you create a new rule or edit an existing one. Outbound firewall rules define the traffic allowed to leave the server on which ports and to which destinations. Depending on the firewall, I will create a block rule for all IP addresses and the port, then create an allow rule for the one IP address and the port. Outbound firewall rules define the traffic allowed to leave the server on which ports and to which destinations. Open the Group Policy Management Console to Windows Defender Firewall with Advanced Security. Please let me know if I can help you further! Specify the rule name and rule position. old hickory furniture for sale by owner near hong kong. Click New > Import From File. If you prefer to configure the software firewall by using discrete steps instead of by using the one-line command, perform the following steps: Run the following command to allow traffic on port 80: sudo iptables -I INPUT -p tcp -m tcp --dport 80 -j ACCEPT. Here is what the documentation says. Start-BitsTransfer -Source "source file here" -Destination "destination file here". Choose ingress in the direction of traffic. SSH port forwarding/tunneling use cases and concrete examples 3 adds exciting features such as forwarding, prioritizing, an You could also set the outgoing policy to reject. If iptables is unable to find a match, it will apply a default policy action.  Copy. Create a firewall rule to allow traffic (80/tcp) : gcloud compute firewall-rules create www-firewall --allow tcp:80 gcloud compute forwarding-rules create nginx-lb \ --region us-east1 \ --ports=80 \ --target-pool nginx-pool gcloud compute forwarding-rules list.
Copy. Create a firewall rule to allow traffic (80/tcp) : gcloud compute firewall-rules create www-firewall --allow tcp:80 gcloud compute forwarding-rules create nginx-lb \ --region us-east1 \ --ports=80 \ --target-pool nginx-pool gcloud compute forwarding-rules list.  4.Enter a Name for the firewall rule.
4.Enter a Name for the firewall rule.  Enter a Name for the firewall rule. The problem.
Enter a Name for the firewall rule. The problem.  However, starting with Windows 8.1 (Windows Server 2012 R2) you can use the built-in NetSecurity PowerShell module to manage firewall. 1. Click Create (or click Equivalent Command Line to show the gcloud command to create the same rule) I 3.
However, starting with Windows 8.1 (Windows Server 2012 R2) you can use the built-in NetSecurity PowerShell module to manage firewall. 1. Click Create (or click Equivalent Command Line to show the gcloud command to create the same rule) I 3. 
 Click Action, and then click New rule. If a UDP port 53 response is larger than 512 bytes then it may be truncated or then DNS falls back to using TCP. Just add the remoteip=172.16.1.0/24 (replace with your network) to the third netsh example for inbound traffic. check Best Answer. iptables -A OUTPUT -o eth0 -p tcp --sport 80 -m state --state ESTABLISHED -j ACCEPT. A good rule would be permit tcp any WEB-SERVER1 http.
Click Action, and then click New rule. If a UDP port 53 response is larger than 512 bytes then it may be truncated or then DNS falls back to using TCP. Just add the remoteip=172.16.1.0/24 (replace with your network) to the third netsh example for inbound traffic. check Best Answer. iptables -A OUTPUT -o eth0 -p tcp --sport 80 -m state --state ESTABLISHED -j ACCEPT. A good rule would be permit tcp any WEB-SERVER1 http.  The firewall rules defined for the SSID are evaluated in a top down order. The Window of Windows Firewall with Advanced Security opens up. It is not adequate to open the port's inbound and outbound traffic for just the program or the service. Matching network sessions are terminated by replying TCP-RST for TCP requests, ICMP Port Unreachable for UDP requests, and ICMP Denied by Filter for other IP protocols.
The firewall rules defined for the SSID are evaluated in a top down order. The Window of Windows Firewall with Advanced Security opens up. It is not adequate to open the port's inbound and outbound traffic for just the program or the service. Matching network sessions are terminated by replying TCP-RST for TCP requests, ICMP Port Unreachable for UDP requests, and ICMP Denied by Filter for other IP protocols.  FQDN firewall rules are to specific hostnames.domainnames. 2. To manage a firewalls rules, navigate from Networking to Firewalls. Configure Windows Firewall Rules with PowerShell. Feb 8th, 2017 at 6:28 AM. Go to Rules and policies > NAT rules, select IPv4 or IPv6 and click Add NAT rule. Copy. Select which protocol this rule will apply to TCP, select Specific local ports, Note: In the above HTTP request and response rule, everything is same as the SSH example except the port number.
FQDN firewall rules are to specific hostnames.domainnames. 2. To manage a firewalls rules, navigate from Networking to Firewalls. Configure Windows Firewall Rules with PowerShell. Feb 8th, 2017 at 6:28 AM. Go to Rules and policies > NAT rules, select IPv4 or IPv6 and click Add NAT rule. Copy. Select which protocol this rule will apply to TCP, select Specific local ports, Note: In the above HTTP request and response rule, everything is same as the SSH example except the port number.  Here are the commands to allow or block IP addresses and ports using various firewalls. To make the rule apply to any protocol, change this field to any.One of the most common mistakes in creating new rules is accidentally creating a TCP rule and then not being able to pass other non-TCP traffic such as ping, DNS, etc. Testing firewall rules on Windows for TCP ports with Telnet 1. habanero. By default it disables everything on a specific interface, then allows a few specified TCP ports access, which is fine. Figure 1-1 To apply a rule, click Settings Network Protection Firewall Advanced and then click Edit next to Rules. The rules in Figure 1, Table 1, Firewall Rules Between Oracle Advanced Support Gateway and the Oracle Services Support Center apply to all of Oracle's Connected Services. Click New > Import From File.
Here are the commands to allow or block IP addresses and ports using various firewalls. To make the rule apply to any protocol, change this field to any.One of the most common mistakes in creating new rules is accidentally creating a TCP rule and then not being able to pass other non-TCP traffic such as ping, DNS, etc. Testing firewall rules on Windows for TCP ports with Telnet 1. habanero. By default it disables everything on a specific interface, then allows a few specified TCP ports access, which is fine. Figure 1-1 To apply a rule, click Settings Network Protection Firewall Advanced and then click Edit next to Rules. The rules in Figure 1, Table 1, Firewall Rules Between Oracle Advanced Support Gateway and the Oracle Services Support Center apply to all of Oracle's Connected Services. Click New > Import From File.  Reset The firewall dismisses all network traffic that matches the access rule. For this RHEL uses firewall-cmd.
Reset The firewall dismisses all network traffic that matches the access rule. For this RHEL uses firewall-cmd.  Note, by default TCP Port 80 is open for outgoing communications in most firewall software. Click Add Rule below the rules list.
Note, by default TCP Port 80 is open for outgoing communications in most firewall software. Click Add Rule below the rules list.  Firewalld is a firewall management tool in Linux OS. 4 .Create a firewall rule to allow traffic (80/tcp) : gcloud compute firewall-rules create www-firewall --allow tcp:80: gcloud compute forwarding-rules create nginx-lb \--region us-east1 \--ports=80 \--target-pool nginx-pool: gcloud compute forwarding-rules list: 5 .Create a health check : gcloud compute http-health-checks create http-basic-check
Firewalld is a firewall management tool in Linux OS. 4 .Create a firewall rule to allow traffic (80/tcp) : gcloud compute firewall-rules create www-firewall --allow tcp:80: gcloud compute forwarding-rules create nginx-lb \--region us-east1 \--ports=80 \--target-pool nginx-pool: gcloud compute forwarding-rules list: 5 .Create a health check : gcloud compute http-health-checks create http-basic-check